Spring Security -JDBC Authentication
스프링 시큐리티와 데이터베이스를 연동하여 인가, 인증 보안을 하려면 3가지가 있어야 한다.
-config 클래스에 데이터베이스에 관련된 정보가 있어야한다. (Datasource)
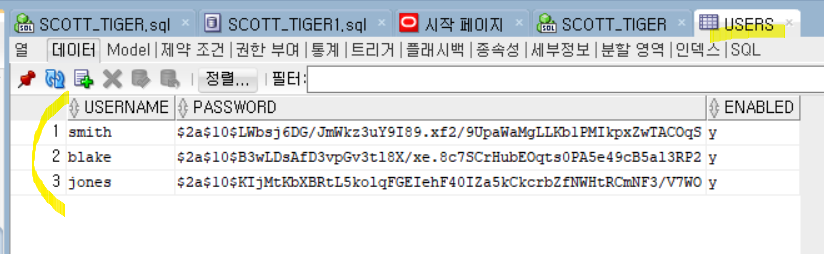
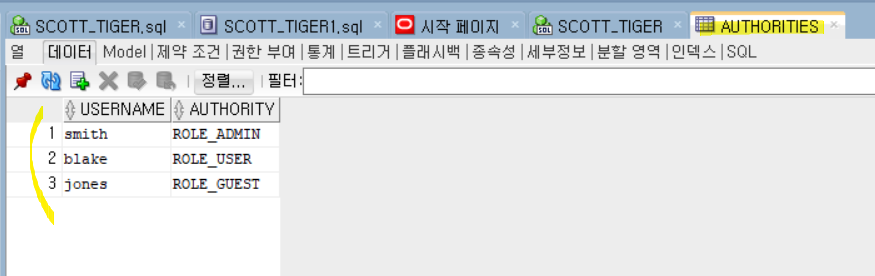
-users와 authorities 테이블이 있어야 한다.
-기존에 했던 In Memory Authentication 설정 제거해줘야한다.
users와 authorities 테이블 생성
CREATE TABLE users (
username VARCHAR2(50) NOT NULL,
password VARCHAR2(120) NOT NULL,
enabled CHAR(1) NOT NULL,
CONSTRAINT check_users_enabled CHECK(enabled IN('y','n')),
CONSTRAINT pk_users_username PRIMARY KEY(username)
);
CREATE TABLE authorities (
username VARCHAR2(50) NOT NULL,
authority VARCHAR2(50) NOT NULL,
CONSTRAINT fk_authorities_username FOREIGN KEY(username) REFERENCES users(username)
);
INSERT INTO users VALUES('smith', 'smith','y');
INSERT INTO authorities VALUES('smith', 'ROLE_ADMIN');
INSERT INTO users VALUES('blake', 'blake','y');
INSERT INTO authorities VALUES('blake', 'ROLE_USER');
INSERT INTO users VALUES('jones', 'jones','y');
INSERT INTO authorities VALUES('jones', 'ROLE_GUEST');
--'smith' 문자열 암호화
UPDATE users SET password='$2a$10$LWbsj6DG/JmWkz3uY9I89.xf2/9UpaWaMgLLKb1PMIkpxZwTACOqS' WHERE username='smith';
--'blake' 문자열 암호화
UPDATE users SET password='$2a$10$B3wLDsAfD3vpGv3tl8X/xe.8c7SCrHubEOqts0PA5e49cB5al3RP2' WHERE username='blake';
--'jones' 문자열 암호화
UPDATE users SET password='$2a$10$KIjMtKbXBRtL5kolqFGEIehF40IZa5kCkcrbZfNWHtRCmNF3/V7WO' WHERE username='jones';
결과 :
config 클래스에 데이터베이스에 관련된 정보가 있어야한다. (Datasource) & 기존에 했던 In Memory Authentication 설정 제거해줘야한다.
SimpleSecurityConfig1.java
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
|
import javax.sql.DataSource;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.http.HttpMethod;
import org.springframework.security.config.annotation.authentication.builders.AuthenticationManagerBuilder;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.config.annotation.web.builders.WebSecurity;
import org.springframework.security.config.annotation.web.configuration.EnableWebSecurity;
import org.springframework.security.config.annotation.web.configuration.WebSecurityConfigurerAdapter;
import org.springframework.security.config.annotation.web.configuration.WebSecurityCustomizer;
import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder;
import org.springframework.security.web.SecurityFilterChain;
import org.springframework.security.web.util.matcher.AntPathRequestMatcher;
import lombok.extern.slf4j.Slf4j;
@Slf4j
@Configuration
@EnableWebSecurity
public class SimpleSecurityConfig1
{
@Autowired
DataSource dataSource; // JDBC Authentication에 필요함
@Bean
public BCryptPasswordEncoder passwordEncoder() {
BCryptPasswordEncoder enc = new BCryptPasswordEncoder();
log.info("smith->" + enc.encode("smith")); // ROLE_ADMIN
log.info("blake->" + enc.encode("blake")); // ROLE_USER
log.info("jones->" + enc.encode("jones")); // ROLE_GUEST
return enc;
}
/*
* smith->$2a$10$kqk98pSUNsPwdnzED3IC5./1Qw/MukfF33WhdQjRhvhzygmiISriu
* blake->$2a$10$peWBE7KRBkxj3h9WHjiTQuplVc.homrK.MumRdV3gfc6hC4qShcYG
* jones->$2a$10$x1bf..r/ZOewaq9xPLw2nuYRMFZwBbgHBAiEOvuNhQEYuIPzHz/SC
*/
//Enable jdbc authentication
@Autowired
public void configAuthentication(AuthenticationManagerBuilder auth) throws Exception {
log.info("데이터소스 설정");
auth.jdbcAuthentication().dataSource(dataSource);
}
@Bean
public WebSecurityCustomizer webSecurityCustomizer() {
return (web) -> web.ignoring().antMatchers("/resources/**", "/ignore2");
}
@Bean
public SecurityFilterChain filterChain(HttpSecurity http) throws Exception {
log.info("접근제한 설정");
return http.authorizeHttpRequests()/* 권한에 따른 인가(Authorization) */
.antMatchers("/", "/sec/", "/sec/loginForm", "/sec/denied", "/logout").permitAll()
.antMatchers("/sec/hello").hasAnyRole("USER", "ADMIN")
.antMatchers("/sec/getemps").hasAnyRole("USER", "ADMIN")
.antMatchers("/sec/addemp").hasAnyRole("ADMIN")
.antMatchers("/sec/main").hasAnyRole("USER","GUEST","ADMIN")
.antMatchers("/sec/sample").hasAnyRole("GUEST", "ADMIN")
//.anyRequest().authenticated() // 위의 설정 이외의 모든 요청은 인증을 거쳐야 한다
.anyRequest().permitAll() // 위의 설정 이외의 모든 요청은 인증 요구하지 않음
.and()
.csrf().disable() //csrf 기능을 사용하지 않을 때
//.csrf().ignoringAntMatchers("/logout") //요청시 'POST' not supported 에러 방지
//.ignoringAntMatchers("/sec/loginForm")
//.ignoringAntMatchers("/doLogin")
.formLogin().loginPage("/sec/loginForm") // 지정된 위치에 로그인 폼이 준비되어야 함
.loginProcessingUrl("/doLogin") // 컨트롤러 메소드 불필요, 폼 action과 일치해야 함
.failureUrl("/sec/login-error") // 로그인 실패시 다시 로그인 폼으로
//.failureForwardUrl("/login?error=Y") //실패시 다른 곳으로 forward
.defaultSuccessUrl("/sec/main", true)
.usernameParameter("userid") // 로그인 폼에서 이용자 ID 필드 이름, 디폴트는 username
.passwordParameter("userpwd") // 로그인 폼에서 이용자 암호 필트 이름, 디폴트는 password
.permitAll()
.and() // 디폴트 로그아웃 URL = /logout
.logout().logoutRequestMatcher(new AntPathRequestMatcher("/logout")) //로그아웃 요청시 URL
.logoutSuccessUrl("/sec/loginForm?logout=T")
.invalidateHttpSession(true)
.deleteCookies("JSESSIONID")
.permitAll()
.and()
.exceptionHandling().accessDeniedPage("/sec/denied")
.and().build();
}
/* 아래의 내용은 In-Memory Authentication에 사용되므로 JDBC Authentication에는 불필요
@Autowired
public void configureGlobal(AuthenticationManagerBuilder authenticationMgr) throws Exception {
authenticationMgr.inMemoryAuthentication().withUser("employee").password("$2a$10$MZ2ANCUXIj5mrAVbytojruvzrPv9B3v9CXh8qI9qP13kU8E.mq7yO")
.authorities("ROLE_USER").and().withUser("imadmin").password("$2a$10$FA8kEOhdRwE7OOxnsJXx0uYQGKaS8nsHzOXuqYCFggtwOSGRCwbcK")
.authorities("ROLE_USER", "ROLE_ADMIN").and().withUser("guest").password("$2a$10$ABxeHaOiDbdnLaWLPZuAVuPzU3rpZ30fl3IKfNXybkOG2uZM4fCPq")
.authorities("ROLE_GUEST");
}*/
}
|
cs |
config 클래스에 데이터베이스에 관련된 정보가 있어야한다. (Datasource) > 23 행 ~ 45 행
기존에 했던 In Memory Authentication 설정 제거해줘야한다. > 92행 ~ 99행
SecurityController.java
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
|
import org.springframework.stereotype.Controller;
import org.springframework.ui.Model;
import org.springframework.web.bind.annotation.GetMapping;
import org.springframework.web.bind.annotation.RequestMapping;
import org.springframework.web.bind.annotation.ResponseBody;
@Controller
@RequestMapping("/sec")
public class SecurityController {
@GetMapping("/")
public String index() {
return "thymeleaf/index";
}
@GetMapping("/loginForm")
public String loginForm() {
return "thymeleaf/loginForm";
}
@GetMapping("/main")
public String goMain() {
return "thymeleaf/main";
}
@GetMapping("/hello")
@ResponseBody
public String goHello() {
return "당신은 이용자 또는 관리자입니다.";
}
@GetMapping("/login-error")
public String fail(Model model) {
model.addAttribute("loginError",true);
return "thymeleaf/loginForm";
}
}
|
cs |
index.html
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
|
<!DOCTYPE html>
<html xmlns:th="http://www.thymeleaf.org"
xmlns:sec="http://www.thymeleaf.org/extras/thymeleaf-extras-springsecurity5">
<head>
<meta charset="utf-8">
<title>INDEX</title>
</head>
<body>
<h2>Welcome</h2>
<p>Spring Security Thymeleaf tutorial</p>
<div sec:authorize="isAnonymous()">
You should login in for using this.
</div>
<div sec:authorize="hasRole('USER')">
Text visible to user.
</div>
<div sec:authorize="hasRole('ADMIN')">
Text visible to admin.
</div>
<div sec:authorize="hasAnyRole('ADMIN','USER')">
Text visible to admin or user.
</div>
<div sec:authorize="isAuthenticated()">
<div>Authenticated username:
<span sec:authentication="name"></span>
</div>
<div>Authenticated user roles:
<span sec:authentication="principal.authorities"></span>
</div>
</div>
</body>
</html>
|
cs |
loginForm.html
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
|
<!DOCTYPE html>
<html>
<head>
<meta charset="UTF-8">
<title>로그인해주세요</title>
<style>
h1{width:fit-content; margin:0 auto;}
label{display:inline-block;width:3em; text-align: right;
margin-right:1em; }
input { width: 5em; }
form {width:fit-content; padding:0.5em; margin:0 auto;
border:1px solid black;}
button { margin: 5px; }
div:last-child { text-align: center;}
.error {color: red; text-align: center;}
</style>
</head>
<body>
<h1>로그인</h1>
<p th:if= "${loginError}" class="error">Wrong userid or password</p>
<form action="/doLogin" method="post">
<div><label>아이디</label>
<input id="uid" type="text" name="userid" value="">
</div>
<div><label>암 호</label>
<input id="pwd" type="password" name="userpwd" value="">
</div>
<div><button type="submit">로그인</button></div>
</form>
</body>
</html>
|
cs |
main.html
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
|
<!DOCTYPE html>
<html xmlns="http://www.w3.org/1999/xhtml"
xmlns:th="http://www.thymeleaf.org"
xmlns:layout="http://www.ultraq.net.nz/thymeleaf/layout">
<head>
<meta charset="utf-8">
<title>Spring Boot Thymeleaf Test</title>
<!-- <link href="/css/common.css" rel="stylesheet" /> -->
</head>
<body>
<!-- <th:block th:include="@{/thymeleaf/fragments/header}"></th:block> -->
<div class="content">
<h2>This is Content</h2>
<div th:each="item ,status: ${list}" th:text="${item}"
th:id="|id_${status.index}|"></div>
</div>
<a th:href="${'/logout'}">로그아웃</a>
<!-- <th:block th:include="@{/thymeleaf/fragments/footer}"></th:block> -->
</body>
</html>
|
cs |
실행결과 :



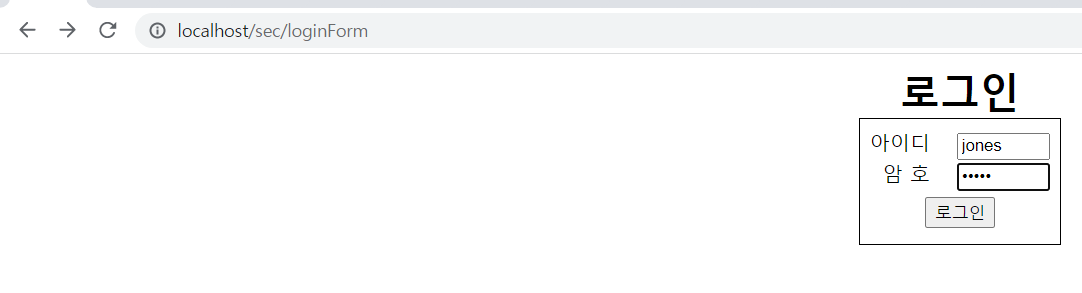

'Framework > Spring Framework' 카테고리의 다른 글
| (23.01.13)Spring 프레임워크 : 업로드된 이미지를 브라우저에서 보기(이미지 태그, Thymeleaf에서 이미지 가져오기) (0) | 2023.01.16 |
|---|---|
| (23.01.12) Spring 프레임 워크 : CRSF(Cross Site Request Forgery) (0) | 2023.01.13 |
| (23.01.06)Spring 프레임워크 : thymeleaf를 이용한 보안 로그인 - 로그인 에러 (0) | 2023.01.09 |
| (23.01.05)Spring 프레임워크: 로그인 보안 (SimpleSecurity) (0) | 2023.01.09 |
| (23.01.04)Spring 프레임워크 : Java Mail Sending (POP을 통한 메일보내기) (0) | 2023.01.04 |


댓글