스프링 부트 2 버전을 사용하다가 3로 마이그레이션 하게 되면 여러가지 이슈가 생기게 된다. 특히나 JDK17 까지 사용하게 되면서 기존에 있던 패키지 경로를 못 쓰게 되는 경우도 많다.
여러가지 문제점에 대해서 어떻게 해결했는지 기록으로 남겨 놓아야겠다.
| 기존 | 변경 후 | |
| 스프링 부트 버전 | 2.7.17 | 3.0.11 |
| 자바 버전 | 8 | 17 |
| JWT 버전 | 0.9.1 | 0.11.5 |
Spring Security 둘 모두 6버전(6:3.1.1.RELEASE) 을 사용하였다.
thymeleaf에서 Spring Security를 쓰려면 springsecurity6를 써야 한다.
🐘 build.gradle
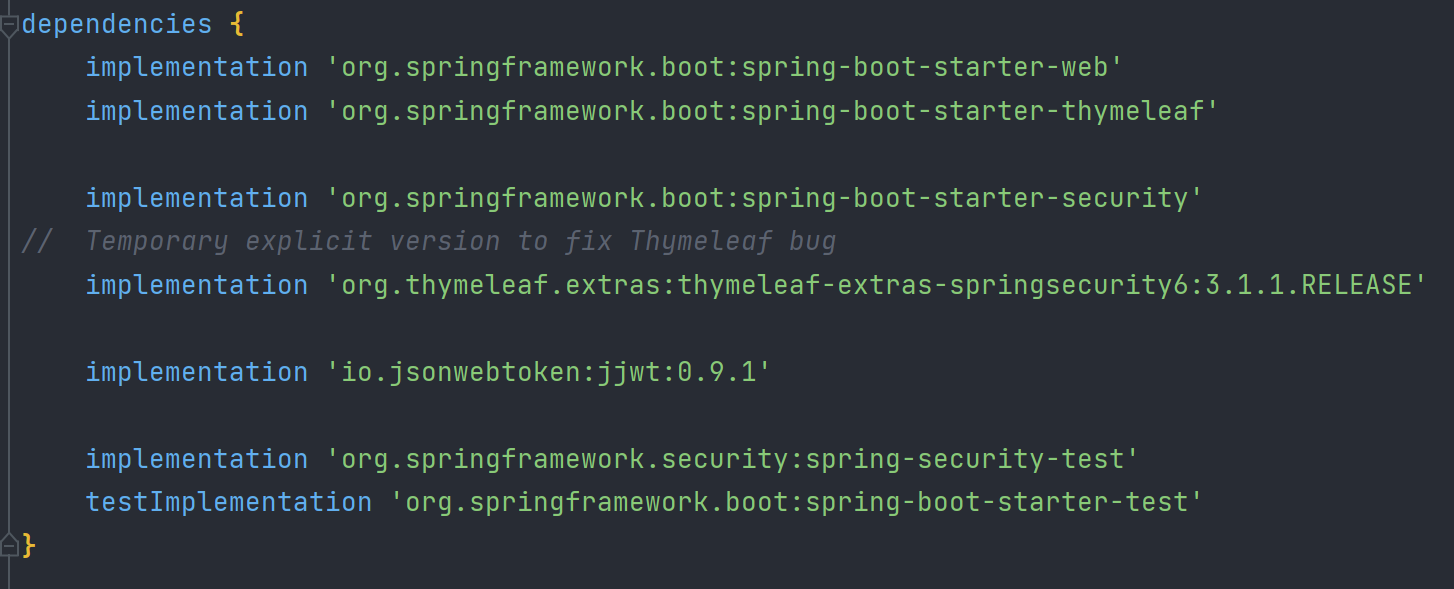
변경 후
dependencies {
implementation 'org.springframework.boot:spring-boot-starter-web'
implementation 'org.springframework.boot:spring-boot-starter-thymeleaf'
implementation 'org.springframework.boot:spring-boot-starter-security'
// Temporary explicit version to fix Thymeleaf bug
implementation 'org.thymeleaf.extras:thymeleaf-extras-springsecurity6:3.1.1.RELEASE'
implementation 'io.jsonwebtoken:jjwt:0.9.1'
implementation 'org.springframework.security:spring-security-test'
testImplementation 'org.springframework.boot:spring-boot-starter-test'
}
WebSecurityConfig

@Bean
public SecurityFilterChain securityFilterChain(HttpSecurity http)
throws Exception {
http.authorizeHttpRequests()
.requestMatchers("/", "/home", "/join", "/login")
.permitAll()
.anyRequest().authenticated()
.and()
.formLogin().disable()
.csrf().disable()
.addFilterBefore(new JwtAuthenticationFilter(jwtTokenProvider()),
UsernamePasswordAuthenticationFilter.class);
return http.getOrBuild();
}
변경 후 .authorizeRequests가 .authorizeHttpRequests로 바뀌었고 .antMatchers() 메소드가 사라지고 .requestMatchers() 로 변경 되었다.
.build()대신 .getOrBuild() 를 사용
javax 패키지
JDK17로 변경하였기 때문에 javax가 사라지고 기본으로 jakarta 패키지로 변경해주어야합니다.


JWT 발급

public class JwtTokenProvider {
private String secretKey = "sleep+mbti";
private long tokenValidTime = 30* 60 * 1000L; // 30min
private Key key;
@Autowired
private UserDetailsService userDetailsService;
// @PostConstruct
// public void init() {
// secretKey = Base64.getEncoder()
// .encodeToString(secretKey.getBytes());
// }
@PostConstruct
public void init() {
String base64EncodedSecretKey = Base64.getEncoder().encodeToString(secretKey.getBytes());
byte[] keyBytes = Decoders.BASE64.decode(base64EncodedSecretKey);
this.key = Keys.hmacShaKeyFor(keyBytes);
}
public String createToken(String username, Collection<? extends GrantedAuthority> roles) {
Claims claims = Jwts.claims().setSubject(username);
claims.put("roles", roles);
Date now = new Date();
return Jwts.builder()
.setClaims(claims)
.setIssuedAt(now)
.setExpiration(new Date(now.getTime() + tokenValidTime))
.signWith(key, SignatureAlgorithm.HS256)
//.signWith(secretKey, SignatureAlgorithm.HS256)
.compact();
}
}
jjwt 0.11.5로 바뀌면서 .signWitH() 메소드가 변경되었다. 기존에는 알고리즘과 인코딩되어 문자열화 시킨, 비밀키 문자열을 파라미터로 넣어주었는데, 0.11.5 버전에선 인코딩된 Key 객체와 알고리즘 순서로 넣어주어야 한다.
Key객체와 파라미터 순서 변경점이 생겼다.
하지만 변경 후에도 실행하면 이런 오류가 나올 것이다.
Caused by: io.jsonwebtoken.security.WeakKeyException: The specified key byte array is 128 bits which is not secure enough for any JWT HMAC - SHA algorithm. The JWT JWA Specification (RFC 7518, Section 3.2) states that keys used with HMAC-SHA algorithms MUST have a size >= 256 bits (the key size must be greater than or equal to the hash output size). Consider using the io.jsonwebtoken.security.Keys#secretKeyFor(SignatureAlgorithm) method to create a key guaranteed to be secure enough for your preferred HMAC-SHA algorithm. See https://tools.ietf.org/html/rfc7518#section-3.2 for more information.

이 오류는 바로 전과는 다르게 이젠 비밀키의 바이트 크기 제한이 생겨서 나타나는 오류이다. 기존에는 짧은 문자열의 시크릿 키여도 작동했지만, 이젠 너무 짧으면 약한 키라는 오류가 터져서 실행이 안된다.
쉽게 말해 우리가 어떤 웹사이트 회원가입 하려할때 비밀번호 6글자를 치면 비밀번호는 10글자 이상이여야합니다. 라는 오류가 나오면서 회원가입을 못하는 것과 같다.
영어는 1글자당 1바이트이고, 한글은 1글자당 3바이트 니깐 한글로 해서 바이트 수를 늘려보았다.
private String secretKey = "ㅏㅣ머래ㅑ절 ㅓㅈ바ㅣ러ㅐ머ㅐㅓㅣㅏ너리ㅏ널;ㅐ머러ㅣ나러ㅣ러재러재러나ㅓ리널ㅈㄷ랴ㅓ호마ㅣㅗ하ㅣ;홀잴ㅈ";
다음과 같이 비밀키를 길게 하여 다시 실행하니 정상 작동하였다.


'Framework > Spring Framework' 카테고리의 다른 글
| JPA 엔티티 상태 (생명주기) (0) | 2024.06.06 |
|---|---|
| 필터와 인터셉터의 차이 (0) | 2024.03.04 |
| JPA 와 Spring data JPA 차이점 (+ 하이버네이트) (0) | 2023.11.08 |
| 요청이 왔을 때 스프링 MVC 내부적 흐름 과정 (DispatcherServlet 중심) (0) | 2023.10.31 |
| (23.01.18)Spring 프레임워크 + Thymeleaf 로 FullCalendar 이미지 나타내기 및 이벤트 온클릭(onClick)처리하기 (0) | 2023.01.23 |


댓글